Threat Intelligence, commonly referred to as “Threat Intel” or “Cyber Threat Intelligence” (CTI), is extensive & useful threat data that people can use to stop & neutralize cyber-attacks against their companies.
Cyber Security Teams can become more proactive by using Threat Intelligence to take quick & data-driven action to stop cyberattacks before they even happen. Moreover, it helps boost an organization's ability to identify & stop active attacks.
Threat Intelligence is created by security analysts by compiling unfiltered threat & security-related data from various sources, evaluating & correlating the information to find patterns, trends, and connections. As a result, they can offer a comprehensive picture of the risks that are real or could arise. The intelligence results are as follows:
- Organization-Specific: It focuses on specific vulnerabilities in the attack surface of the business, the attacks they enable, and the assets they expose rather than on generalities.
- Detailed & Contextual: It includes threats that are directed at the company & hackers that could carry them out, the Tactics, Techniques, and Procedures (TTPs) that these hackers might employ, and Indicators of Compromise (IoCs) that could indicate a specific cyberattack.
- Actionable: Information Security Teams can use it to address vulnerabilities, rank risks, take corrective action, and assess new or current cybersecurity products.
The average cost of a data breach to its victims is $4.35 million, according to IBM's Cost of a Data Breach 2022 research. The largest cost percentage ($1.44 Million) is credited to the attacks’ detection & escalation expenses. Threat Intelligence can lower detection costs & minimize the effect of successful breaches by giving security teams the knowledge they need to identify attacks sooner.
Types of Threat Intelligence
Threat Intelligence comes in various forms, ranging from high-level, non-technical data to technical specifics of individual attacks. Here are some categories of Threat Intelligence you should be aware of:
- Strategic Threat Intelligence: This high-level information provides conditions for the threat. It’s non-technical data that a company could provide to the board of directors. The risk analysis of how a business action might expose the company assets to cyberattacks is an example of Strategic Threat Intelligence.
- Tactical Threat Intelligence: It includes the details of how threats are being executed & defended against, including attack vectors, tools, and infrastructures attackers are using, types of businesses or technologies that are targeted, and avoidance strategies. It also helps an organization understand how likely they are to be a target for different types of attacks.
- Operational Threat Intelligence: An IT department can use this information to take precise action against an attack as part of Active Threat Management. It details the attacking strategy, attack kind, and attack timing. Also, it is difficult to collect this information, as it is best obtained directly from the attackers.
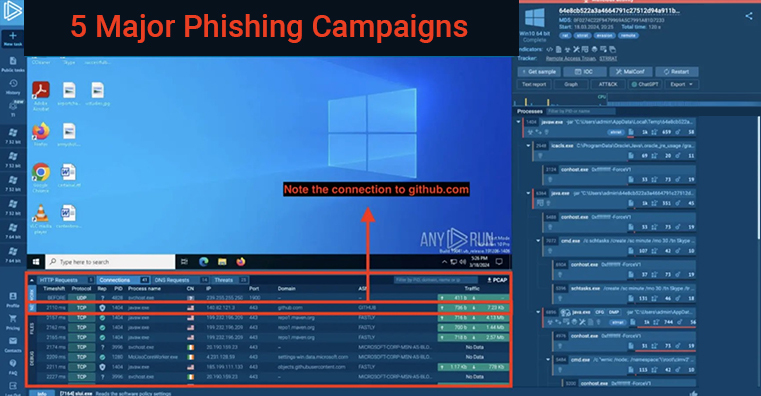
- Technical Threat Intelligence: It collects specific proof that an attack is taking place, often known as Indications of Compromise (IOCs). Artificial Intelligence (AI) is used by some Threat Intelligence technologies to search for these signs, which might include C2 infrastructures’ IP addresses or email content from phishing campaigns.
The Threat Intelligence Lifecycle
The process by which security teams create, distribute, and enhance their Threat Intelligence is what we know as the Threat Intelligence Lifecycle. Although the specifics may differ from company to company, the majority of them adhere to this 6-step procedure.
Step 1: Planning
To define the necessary intelligence, security analysts join organizational stakeholders such as department heads, IT and security team members, and executive leaders who are involved in the cybersecurity decision-making process. Typically, these comprise cybersecurity-related queries that stakeholders require or desire responses for.
Step 2: Threat Data Collection
In this, the cyber security team gathers any unprocessed threat information that may contain or add to the answers stakeholders. In keeping with the previous scenario, if a security team is looking into a new ransomware attack, they may collect data on the ransomware gang responsible for it, the kinds of companies they've previously attacked, and their attack routes. This dangerous information may originate from several places, such as insider threats, viruses, worms, botnets, drive-by download attacks, etc.
- Threat Intelligence Feeds — It provides real-time threat data streams. Sometimes the name is deceptive: Some feeds contain raw threat data, while others contain processed or evaluated Threat Intelligence. Usually, security teams follow several commercial and open-source feeds. Each of these streams can help us comprehend risks on a deeper level.
- Information-Sharing Communities — forums, trade associations, and other groups where experts from around the globe exchange personal accounts, observations, and Threat Intelligence. Through the National Council of ISACs (NSI), several industry-specific Information Sharing and Analysis Centers (ISACs) across the US's critical infrastructure sectors collaborate.
- Internal Security Logs — Internal security information from systems for compliance and security, including the ones listed below:
- SIEM (Security Information and Response)
- SOAR (Security Orchestration, Automation and Response)
- EDR (Endpoint Detection & Response)
- XDR (Extended Detection & Response)
- Attack Surface Management (ASM) Systems
This data gives the company a history of the cyberattacks it has encountered and can be used to identify evidence of internal or external risks that were previously missed. Sometimes, data from these various sources is combined into a single dashboard for easier management.
Step 3: Processing
To facilitate analysis, security analysts now compile, normalize, and co-relate the raw data they have collected. This could entail removing false positives or analyzing data related to a prior security event using a Threat Intelligence framework like MITRE ATT&CK. By using Artificial Intelligence (AI) and Machine Learning to correlate threat information from many sources and spot early patterns in the data, many Threat Intelligence tools help automate this process.
Step 4: Analysis
When threat data is analyzed, it transforms from raw data to actual threat information. At this point, security analysts test & validate the trends, patterns, and other insights they may utilize to provide suggestions and respond to security requirements from stakeholders.
Step 5. Dissemination
The relevant stakeholders receive insights & recommendations from the security team. Based on these suggestions, they might take steps, such as creating new SIEM detection rules to target recently discovered IoCs or upgrading firewall blacklists to stop traffic coming from suspected IP addresses.
Step 6. Feedback
Stakeholders & data analysts evaluate whether the requirements were fulfilled at this point by considering the latest Threat Intelligence cycle. Stakeholders may change their priorities, the extent to which they wish to receive intelligent reports, or how data should be presented or disseminated.
Key Components for Actionable Threat Intelligence
Here are some key components you should consider while using Actionable Threat Intelligence:
#1: Threat History Data
A lot of threat history data is necessary for Actionable Threat Intelligence. Machine learning & cyber threat analysis capabilities give important data. But it’s only possible for the Cyber Threat Intelligence to proactively block 10 cyber threats if it only possesses 10 threat data sets. The Threat Intelligence will provide more information about attacks that could harm your network as the data collection grows. Furthermore, as more data is collected, ML-based analytical algorithms will further improve.
#2: Automated Detection/Blocking
Vast threat history data, machine learning powers, and accurate cyber threat analysis are great. However, the Cyber Threat Intelligence system must use these tools to automate actions. To permanently block attacks, it must respond to pre-discovered threats, and take proactive measures for future attacks.
For the foreseeable future, there will probably be an exponential increase in the number of cyber threats. Manual work just cannot keep up with the pace. Due to this, companies need to implement an integrated threat management system to identify a threat in Asia and stop it in South America.
#3: Cyber Threat Analysis
A well-designed cyber threat analysis is a necessity for Cyber Threat Intelligence. Since more data is being handled by businesses than ever before, hackers are more financially motivated than before. This is why they are developing greater sophistication & coordination. This creates additional difficulties that call for more creative approaches to cyber threat assessments.
#4: Machine Learning Capabilities
The number of threats is increasing, and frequent dangers are quickly evolving. These are two alarming developments in threat defense. Cyber Threat Intelligence must use machine learning in threat scenarios to stay up to date with current trends.
Machine Learning can analyze massive data sets to identify trends and anticipate risks. Security Operations Teams can use it to quickly identify and rank advanced threats that need careful human investigation. To enhance their machine learning capabilities, companies are considering the following conditions:
- Dataset Diversification & Precision. For thorough coverage, it is important to show malware that is encountered by companies of diverse sizes, industries, and regions, and that is transmitted through a variety of attack routes.
- Multilayered Processing. To ensure that security teams are dealing with prioritized & context-rich detections, every processing step in a machine learning pipeline should increase the consistency & accuracy of detections.
- Correlation of Endpoint & Network Data. The system should identify more threats quickly, increase precision & self-learning capabilities, and boost detections by connecting the multilayered processing outcomes.
- In-Depth Domain Expertise & Continuously Trained Classifiers. When developing a strong machine-learning system that is difficult to manipulate, domain expertise & ongoing learning are important components of the puzzle.
Who Benefits from Threat Intelligence?
Organizations of all sizes gain from Threat Intelligence by processing threat data to understand attackers, react to incidents quickly, and predict hackers’ next move. Otherwise, this data gives SMBs access to a certain protection level that wouldn’t be possible.
Alternatively, by using external Threat Intelligence and improving their analysts’ efficiency, businesses with large security teams can lower the expense & necessary expertise. Every member of a security team can benefit from Threat Intelligence differently, from top to bottom, including:
- Sec/IT Analyst
- SOC
- CSIRT
- Intel Analyst
- Executive Management
The following are the advantages of each role and the particular use cases that relate to each:
|
Function |
Benefits |
|
Sec/IT Analyst |
Optimize prevention and detection capabilities and strengthen defenses |
|
SOC |
Prioritize incidents based on risk and impact to the organization |
|
CSIRT |
Accelerate incident investigations, management, and prioritization |
|
Intel Analyst |
Uncover and track hackers targeting the organization |
|
Executive Management |
Understand the risks the organization faces and what the options are to address their impact |
Common Indicators of Compromise (ICO)
If security officers check in the correct places for unusual activity, they can find signs that an attack has occurred or is approaching. This is where businesses can use artificial intelligence for assistance. Among the common IOCs are:
- Unusual Privileged User Account Activity: Attackers frequently try to increase their account privileges or switch from a compromised account to one with more authority.
- Login Anomalies: Unauthorized file access attempts made after hours, many unsuccessful login attempts from various IP addresses across the globe to the same account, and unsuccessful login attempts using fictitious user accounts are all signs that something is wrong.
- Increases in Database Read Volume: A significant rise in database read volume may be a sign that an unusual amount of data is being extracted. It may include the credit card numbers stored in a database.
- Unusual Domain Name System (DNS) requests: Red signals include large increases in DNS requests from a particular address and patterns of DNS requests to external hosts. These could indicate that command & control traffic is being sent by someone outside the company.
- Large Numbers of Requests for the Same File: Repeated attacks are a common component of cybercrime. They may be a sign that someone is looking for a weakness. 500 requests for the same file means that multiple people are looking for vulnerabilities.
- Unexplained Configuration or System File Changes: Finding a credit card harvesting tool is hard. However, finding modifications to system files caused by the tool's installation is simpler.
Available Threat Intelligence Tools
Through the open-source community, several Threat Intelligence products are either free to use or accessible for purchase. Their methods for obtaining Threat Intelligence vary slightly among the following:
- Malware Disassemblers: These tools allow security experts to fight against similar attacks in the future by observing malware and learning how it works.
- Security Information & Event Management Tools: Security experts must look after the network in real-time with these tools. It allows security experts to collect data on unusual activity and questionable traffic.
- Network Traffic Analysis Tools: Tools for network traffic analysis gather data about a network and log network activity to create insights that facilitate the intrusions’ identification.
- Threat Intelligence Communities & Resource Collections: Public websites that compile information about threats and known compromise indicators might be a great way to obtain Threat Intelligence. Some of these groups encourage collective research and offer practical guidance on preventing attacks.
Companies can stop a cyberattack before it starts if they are aware of new dangers and know how to avoid them. All companies should include the collection & evaluation of Threat Intelligence in their security plan.
Wrapping It Up
This post explores the idea of Cyber Threat Intelligence (CTI) and highlights how important this tool is to fight cyber threats before they happen. This tool is defined as data analysis of hackers’ objectives & attack patterns, allows preventive security actions, and lowers the costs & consequences of detection.
Also, this post describes the lifecycle of threat intelligence, its different forms, and the essential elements of actionable intelligence. It ends by explaining who gains from Cyber Threat Intelligence, typical signs of compromise, and instruments for threat intelligence that are currently accessible.
Did you find this article interesting? Join our TTB community on LinkedIn for more intriguing articles.





.jpg)