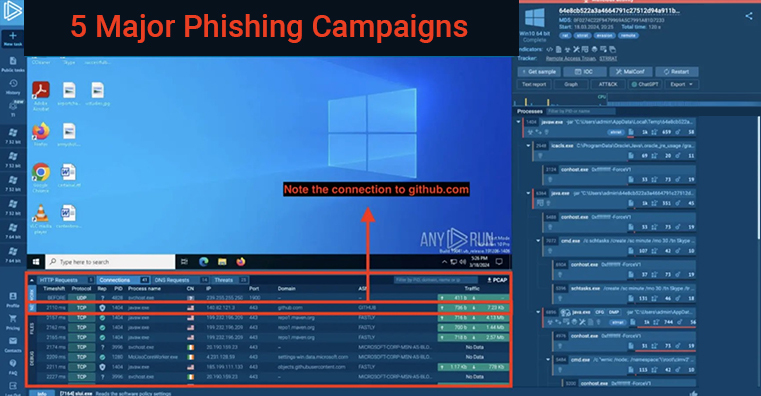
The Open Web Application Security Project (OWASP) highlights the most important online security threats. As a matter of fact, it is an invaluable resource for developers & security experts across the world. Security Logging & Monitoring Failures are among the most important factors affecting incident detection & response, and they are frequently in the top 10 categories.
List of Mapped CWEs
- CWE-117 Incorrect Neutralization for Logs Output: This is the inability to neutralize user-controlled input before logging in. Thus, it can result in sensitive data exposure or log injection attacks.
- CWE-223 Disclosure of Security Information: It draws attention to the dangers of excluding crucial security information from logs. As a result, it becomes more difficult for the cyber experts to identify & fix the security issues.
- CWE-532 Placement of Private Data in the Log File: It draws attention to the danger due to the unintentional logging of private data. Thus, hackers can use such data against use if the log files are compromised.
- CWE-778 Insufficient Logging: CWE-778 indicates insufficient logging methods, which prevents sufficient visibility into their operations & security breaches. Also, it impedes incident detection & response efforts.
CWE = Common Weakness Enumeration
Factors Affecting the Common Weakness Enumeration
|
CWEs Mapped |
Max. Incidence Rate |
Avg. Weighted Rate |
Avg. Weighted Exploit |
Avg. Weighted Impact |
Max. Coverage |
Avg. Coverage |
Total Occurrences |
Total CVEs |
|
4 |
19.23 |
6.51% |
6.87 |
4.99 |
53.67% |
39.97% |
53,615 |
242 |
Importance of Logging & Monitoring
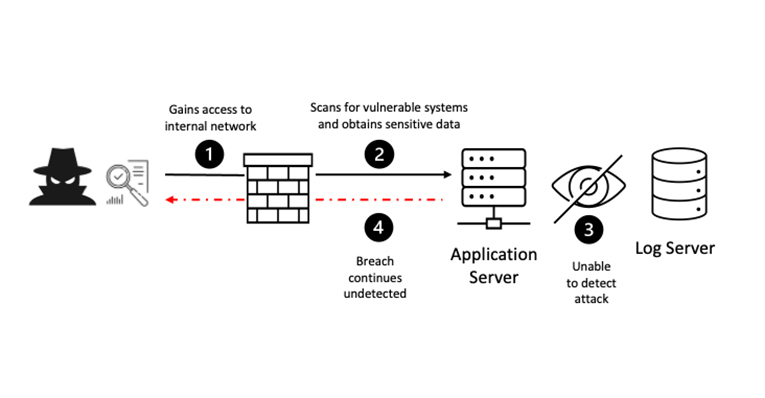
Imagine a cyber attack on your system. If you weren’t regularly monitoring & logging security incidents, you wouldn’t even know that it is happening. Failure in logging & monitoring precisely may cause such situations. Here are a few cyber dangers listed by OWASP:
The Cost of Failure:
Failure in security logging & monitoring might cause serious consequences like reputational harm, legal penalties, data breaches, and lost customer confidence.
Protecting Yourself:
Now the question arises - how can you improve your security measures? Well, you can follow the below actions to protect your systems:
- Record the important events carefully.
- Check if the logs have sufficient information.
- Use a centralized log management & monitoring system.
- Configure automated notifications if any questionable activity occurs.
- Check the logs at regular intervals and perform penetration & evaluation tests.
- Educate your team on incident response techniques.
You can enhance the ability to identify & respond to security issues by fixing these flaws and placing appropriate logging & monitoring procedures. It will eventually secure your company and its data.
Examples of Attack Scenarios:
- Scenario 1: A significant data breach on a major Indian airline involved millions of customers’ personal information which spanned more than 10 years. After some time, the airline noted the data breach by a 3rd party cloud hosting provider where the incident took place.
- Scenario 2: A significant European airline experienced a reportable GDPR violation. As per the reports, hackers stole nearly 400,000 client payment records by taking advantage of payment application’s security flaws. As a result, the privacy regulator put a fine on the airline with 20 million pounds.
Remember: Maintaining security isn’t a one-time event; it's a continuous event. To stay ahead of emerging threats & vulnerabilities, regularly check & update your security procedures, including logging & monitoring.
Bonus Tips
- For more in-depth details on security logging & monitoring issues and other security threats, check out the OWASP Top 10.
- Consider using open-source solutions for log management & analysis, such as Graylog or ELK Stack.
- To keep your team ready, take part in security awareness training programs & drills on a regular basis.
You can ensure that your company is better prepared to handle the constantly evolving panorama of cyber threats by addressing security logging & monitoring failures.




.jpg)